记一次时间相差一个月导致 apt install 提示证书有问题 作者: Shine 时间: 2021-07-24 分类: Linux 评论 几个月没登录家里的 NAS 了,主要是我这里的宽带、公司网络都没有 IPv6 只能手机开热点才有 IPv6,连接上家里路由器 VPN 才能访问 今天听说 **江西移动宽带** 不再提供对等上下对等宽带,想来测下速度,但是没有安装 `speedtest-cli`,就直接执行了 `apt install speedtest-cli` 但是安装失败了,大概提示的是: ``` server certificate verification failed. CAfile: /etc/ssl/certs/ca-certificates.crt CRLfile: none ``` 因为我这边已经修好了,并且终端仅保留部分执行历史,所以就没办法贴原文了 ## 解决办法 可能是你的系统时间出现了些问题,你可以使用 `date` 命令查看: ```shell root@Chainedbox:~# date 2021年 06月 14日 星期一 03:50:33 UTC ``` 一看,这个时间相差了一个多月,怪不得报证书问题, 仅需要校准下时间即可 ```shell root@Chainedbox:~# sudo ntpdate -s ntp.aliyun.com root@Chainedbox:~# ntpdate -u ntp.aliyun.com 24 Jul 14:32:15 ntpdate[24105]: step time server 203.107.6.88 offset 3494399.184393 sec root@Chainedbox:~# date 2021年 07月 24日 星期六 14:32:24 UTC ``` ### 终于成功安装 speedtest-cli ``` root@Chainedbox:~# apt install speedtest-cli 正在读取软件包列表... 完成 正在分析软件包的依赖关系树 正在读取状态信息... 完成 下列【新】软件包将被安装: speedtest-cli 升级了 0 个软件包,新安装了 1 个软件包,要卸载 0 个软件包,有 157 个软件包未被升级。 需要下载 19.1 kB 的归档。 解压缩后会消耗 85.0 kB 的额外空间。 获取:1 https://mirrors.tuna.tsinghua.edu.cn/debian stretch/main arm64 speedtest-cli all 1.0.0-1 [19.1 kB] 已下载 19.1 kB,耗时 0秒 (32.6 kB/s) 正在选中未选择的软件包 speedtest-cli。 (正在读取数据库 ... 系统当前共安装有 58082 个文件和目录。) 正准备解包 .../speedtest-cli_1.0.0-1_all.deb ... 正在解包 speedtest-cli (1.0.0-1) ... 正在处理用于 man-db (2.7.6.1-2) 的触发器 ... 正在设置 speedtest-cli (1.0.0-1) ... ```
PandoraBox / OpenWRT 等系统路由器设置 frpc 开机自启 作者: Shine 时间: 2021-07-03 分类: Linux,路由器 评论 ## 背景 今天在租住的地方办了联通宽带(猜测城中村某公司代理的,无公网 IPv6,只能凑合着用)60元/月 50M,最低3个月起办,押金120元,真贵真坑,网络质量一般,不能持续平稳跑满网速 可以让闲置已久的**小爱音响**和**温湿度计**之类的智能设备联动起来了 为了便于远程管理,特地装了个 **frp 内网穿透** ## 正文 假设你的 `frpc` 安装路径在 `/usr/local/frp_0.37.0_linux_mipsle` 将以下内容保存至文件比如 `/usr/local/frp_0.37.0_linux_mipsle/check.sh` > 启动命令记得自己修改! > 启动命令记得自己修改! > 启动命令记得自己修改! ```shell #!/bin/sh # 休眠 5s 再往下执行,谨防重复执行创建大量 frpc 进程,你可以减少睡眠时间 sleep 5 frpc_pid=$(pgrep /usr/local/frp_0.37.0_linux_mipsle/frpc) if test -z "$frpc_pid" then echo "Not running! Try to start" # 启动命令记得自己修改! # 启动命令记得自己修改! # 启动命令记得自己修改! /usr/local/frp_0.37.0_linux_mipsle/frpc -c /usr/local/frp_0.37.0_linux_mipsle/frpc.ini > /dev/null 2>&1 & else echo "It is running, pid: ${frpc_pid}" fi ``` 然后在 系统 -> 计划任务,添加计划任务,运行时间每X分钟运行一次脚本,我这里设置的是 1 分钟执行一次 > **命令**那个表单选择**自定义**,然后粘贴刚刚保存脚本的路径,比如我的是 `/usr/local/frp_0.37.0_linux_mipsle/check.sh`  ### 另外值得一提的是 你还可以在 系统 -> 启动项 添加启动脚本 ```shell /usr/local/frp_0.37.0_linux_mipsle/start.sh ``` 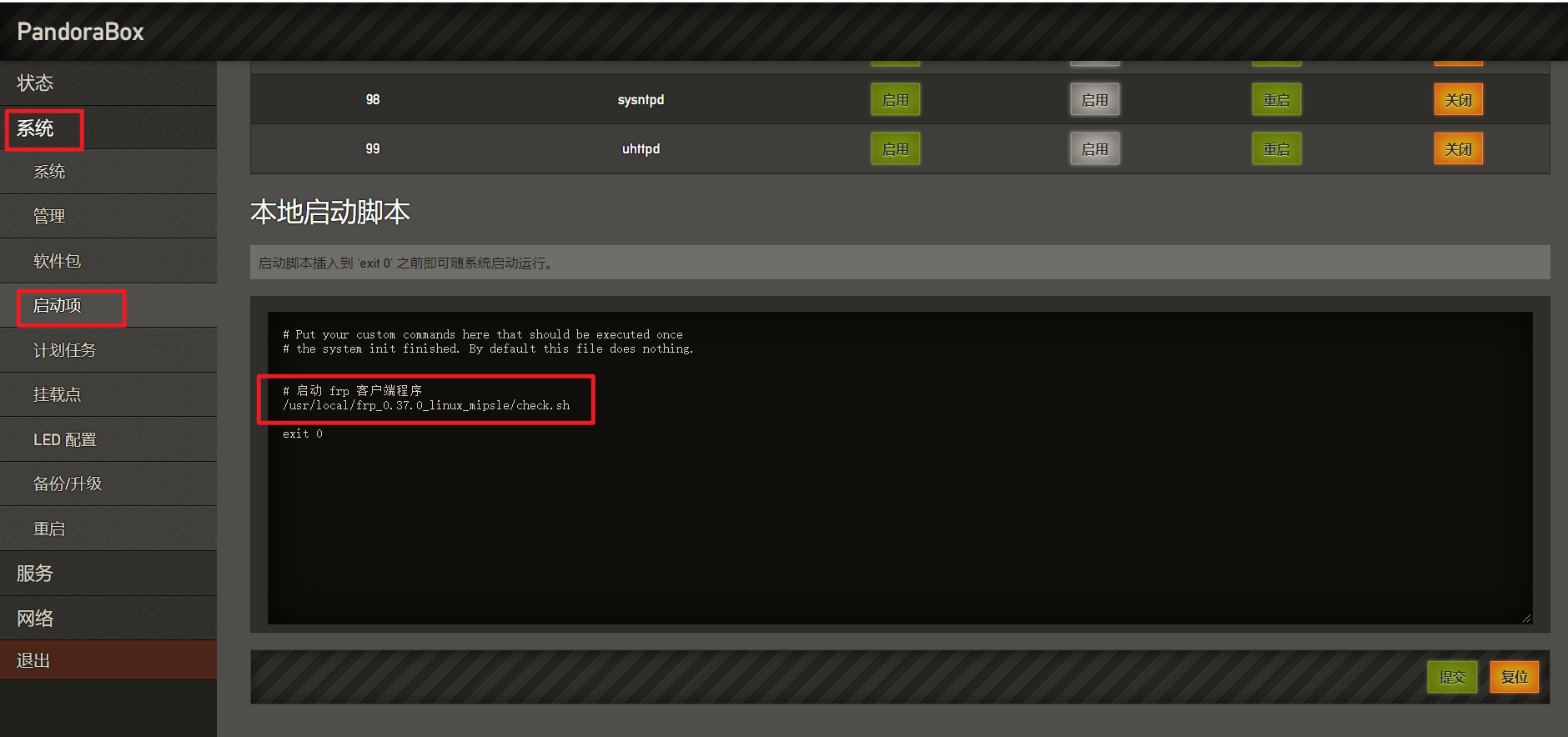
Linux 指定用户执行命令 / Composer 因权限问题导致无法执行 作者: Shine 时间: 2021-05-14 分类: Linux 评论 ## 背景 在网上查到的使用 `su 用户名 -c "命令"` 即可指定用户执行某些命令 但是运行结果是这样的 > This account is currently not available. ```log [root@izvkgq9z www.xxxx.com]# su www -c "composer install" This account is currently not available. ``` 原来设置了该用户不能用以登录 ``` [root@izvkgq9z www.xxxx.com]# cat /etc/passwd | grep www www:x:1000:1000::/home/www:/sbin/nologin ``` ## 解决办法 > 使用 `su 用户名 -s /bin/bash -c "需要执行的命令"` ``` su -s /bin/bash -c "composer install" www ``` --- > 以下是额外话题 ## composer 安装出现新的问题 执行 `composer install` 报了以下错误 ``` [RuntimeException] Could not delete /home/wwwroot/www.xxxx.com/vendor/kylekatarnls/update-helper/composer.json: Directive 'track_errors' is deprecated ``` 大概意思是不能删除文件,然后就想到了权限问题,然后看了下权限信息 ``` [root@izvkgq9z www.xxxx.com]# ll | grep vendor drwxr-xr-x 47 root root 4096 May 14 13:55 vendor ``` 猜测是项目自动构建之类的,权限没弄好,本应该是 `www` 权限的,这个简单了,使用 `chgrp` 和 `chown` 命令改一下 `vender` 目录及其子目录/文件 用户组和所有者 ``` # 更改用户组 chgrp www -R vendor # 更改所有者 chown www -R vendor ```
Linux 相关练习题 作者: Shine 时间: 2020-10-30 分类: Linux 评论 # 以#开头的那一行是注释,不需要运行 # 以#开头的那一行是注释,不需要运行 # 以#开头的那一行是注释,不需要运行 1. ## 创建云服务器,提供能够进行有效连接的公网IP。 --5分 (如果未建立则考试没有成绩) 2. ## 创建 `jjcpxp` 用户,并设置密码为 `12345678` --5分 (如果未建立则考试不能及格) ```bash # 指定 -M 参数时不在 /home 下创建目录 useradd jjcpxp -p 12345678 #小扩展,删除用户可以使用 userdel -r 用户名 ``` 3. ## 创建 `test` 用户,并将用户目录设置为 `/home/jjcpxp` 设置密码为 `123456`. --5分 ```bash # -d /home/jjcpxp # -m useradd test -p 123456 # 修改目录 chown -R test.test /home/jjcpxp ``` 4. ## 用 `test` 用户在 `/home/jjcpxp` 目录下建立 `TXT.sh` 文件,文件内容为批处理建立 `TXT1.txt`、`TXT2.txt`、`TXT3.txt` 文件。 再建立 `del_TXT.sh` 文件文件内容为删除以上建立的3个txt文件,`jjcpxp` 用户可以操作执行。 --10分 ```bash # 登录 test 账户 su - test # 进入 /home/jjcpxp 目录 cd /home/jjcpxp # 创建 TXT.sh 文件 touch TXT.sh # 设置 TXT.sh 文件内容:创建 TXT1.txt、TXT2.txt、TXT3.txt 文件 echo touch TXT1.txt >> TXT.sh echo touch TXT2.txt >> TXT.sh echo touch TXT3.txt >> TXT.sh #################################################### # 再建立 del_TXT.sh 文件 touch del_TXT.sh # 文件内容为删除以上建立3个txt文件 echo rm -rf TXT1.txt >> del_TXT.sh echo rm -rf TXT2.txt >> del_TXT.sh echo rm -rf TXT3.txt >> del_TXT.sh # 设置执行权限 ## 首先切换成 root 用户 su - root cd /home/jjcpxp # 然后再设置文件权限 (jjcpxp 用户可以操作执行) chown jjcpxp del_TXT.sh ``` 5. ## 用 `jjcpxp` 用户在 `/home/jjcpxp` 目录下建立 `Dir.sh` 文件 ,文件内容为建立 `dir1`、`dir2`,`dir3` 的3个文件夹,同时建立 `del_Dir.sh` 文件,文件内容为同时删除上述建立的文件目录。 --10分 ```bash su - jjcpxp touch Dir.sh echo mkdir dir1 >> Dir.sh echo mkdir dir2 >> Dir.sh echo mkdir dir3 >> Dir.sh touch del_Dir.sh echo rm -rf dir1 >> del_Dir.sh echo rm -rf dir2 >> del_Dir.sh echo rm -rf dir3 >> del_Dir.sh ``` 6. ## 建立内容为“!!!欢迎来到[自己姓名]CentOS服务器!!!”登录显示。--5分 ```bash su - root vi /etc/motd # 按键盘上 i 键进入编辑 # 然后删除文 # 然后按 Esc 键,输入 :wq # 然后按回车保存并关闭文件 ``` 7. ## 在 `/home/jjcpxp` 建立一个属主为 `root` 的 `xuehao` 文件,文件内容为`自己的姓名 /学号`:同时在 `/tmp` 目录下建立相同 的文件 且 `jjcpxp` 用户可读 --8分 ```bash su - root touch /home/jjcpxp/xuehao echo 陈文洲/10086 > /home/jjcpxp/xuehao cp /home/jjcpxp/xuehao /tmp # 参考 https://blog.51cto.com/qingmiao/2069603 setfacl -m u:jjcpxp:r /tmp/xuehao ``` 8. ## 统计 `/tmp/linux_test.txt` 文件的前10行文件内容并把内容结果输出到 `/home/jjcpxp` 目录下的 `grep` 文件中 --8分 ```bash touch /tmp/linux_test.txt # 按键盘上 i 键进入编辑 # 自己在里面写15行内容 # 然后按 Esc 键,输入 :wq # 然后按回车保存并关闭文件 vi /tmp/linux_test.txt head -10 /tmp/linux_test.txt > /home/jjcpxp/grep ``` 9. ## 统计云服务器在正在运行的 `.service` 服务结果并将结果输出到 `/home/jjcpxp` 目录下 `service` 文件中 --8分 ```bash ps auxw > /home/jjcpxp/service ``` 10. ## 将 `/etc/sysconfig/` 目录下的树结构结果输出到 `/home/jjcpxp` 目录下的 `tree` 文件中去 -8分 ```bash # 安装 tree 命令 yum install -y tree tree /etc/sysconfig/ > /home/jjcpxp/tree ``` 11. ## 统计 `/etc/sysconfig/network-scripts/ifcfg-eth0` 的文件文件行数并输出到 `/home/jjcpxp/` 目前的 `wc` 中。 再将上述文件的内容输出到 `ifcfg-eth0` 文件中 --8分 ```bash wc -l /etc/sysconfig/network-scripts/ifcfg-eth0 > /home/jjcpxp/wc cat /home/jjcpxp/wc > /home/jjcpxp/ifcfg-eth0 ``` 12. ## 将关机命令、重启命令的3种形式 写入到 `/home/jjcpxp` 目录中的 `shut` 文件中 --5分 ```bash # 关机命令 echo shutdown -h now >> /home/jjcpxp/shut # ## 重启命令 echo shutdown -r now >> /home/jjcpxp/shut ``` 13. ## 测试 www.163.com 网站的联通性并测试10个IMCP包将结果输出到 `/home/jjcpxp` 目录中的 `ping`文件中 --10分 ```bash # -c 参数,指定次数 # > /home/jjcpxp/ping 将结果重定向至 /home/jjcpxp/ping 并覆盖写入文件 ping -c 10 www.163.com > /home/jjcpxp/ping ``` 14. ## 将 `/home/jjcpxp` 目录中的所有文件拷贝到 `/tmp` 目录中 `test` 目录下,所有文件设为 `test` **只读** 属性 --10分 ```bash mkdir /tmp/test cp /home/jjcpxp/* /tmp/test setfacl -m u:jjcpxp:r /tmp/test/* ```
Windows/Linux 等使用 openssl 命令查看网站证书 作者: Shine 时间: 2020-07-09 分类: 其他分类 评论 # 假设我们要查看 `nowtime.cc` 的证书,其 https 端口为 443 执行命令如下: ``` openssl s_client -showcerts -connect nowtime.cc:443 ``` # 运行结果: > 自行提取证书了 `-----BEGIN CERTIFICATE-----` `-----END CERTIFICATE-----` > > 首个是根证书 ``` C:\Users\chuwen>openssl s_client -showcerts -connect nowtime.cc:443 CONNECTED(00000188) depth=1 C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3 verify error:num=20:unable to get local issuer certificate verify return:1 depth=0 CN = nowtime.cc verify return:1 --- Certificate chain 0 s:CN = nowtime.cc i:C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3 -----BEGIN CERTIFICATE----- MIIFWzCCBEOgAwIBAgISBN4DHrdBlbZURCO30zWTHNcqMA0GCSqGSIb3DQEBCwUA MEoxCzAJBgNVBAYTAlVTMRYwFAYDVQQKEw1MZXQncyBFbmNyeXB0MSMwIQYDVQQD ExpMZXQncyBFbmNyeXB0IEF1dGhvcml0eSBYMzAeFw0yMDA2MjcwNTIwNDNaFw0y MDA5MjUwNTIwNDNaMBUxEzARBgNVBAMTCm5vd3RpbWUuY2MwggEiMA0GCSqGSIb3 DQEBAQUAA4IBDwAwggEKAoIBAQDsIEKlS36Aay6UwWHLPYmsu9+3G3EA11236AD+ lLXEhEO4tAuc0FV5nliJ7mlXx9STvTtS/zzLqUDRVcWlBeXiS7UHjkvSN+sUU9rI /osDO/Cd/NXo8DYqwBOZ+2DFX/Um1gi415HN2hEAP3KgbSXRFqiMO5NpXLPBYK7C LtdpRIcvMtLKlFKmAARsqVd61gsN0WqYWaitnpjwGQG75KlhgJXqml6A7CiTikAS JdW4vHg4uONqKnJ2qPK9a3b3L01pgqwU5k/NEmxWUrRFveFDqZTvja4ajgILZ9wG CFUH3+0CpLCVVO7oG5jZ95Y2jzALpyMYotq/iRbxMwfbwhonAgMBAAGjggJuMIIC ajAOBgNVHQ8BAf8EBAMCBaAwHQYDVR0lBBYwFAYIKwYBBQUHAwEGCCsGAQUFBwMC MAwGA1UdEwEB/wQCMAAwHQYDVR0OBBYEFDFRcdtmSz9iTZXpz4D2KNXCqIABMB8G A1UdIwQYMBaAFKhKamMEfd265tE5t6ZFZe/zqOyhMG8GCCsGAQUFBwEBBGMwYTAu BggrBgEFBQcwAYYiaHR0cDovL29jc3AuaW50LXgzLmxldHNlbmNyeXB0Lm9yZzAv BggrBgEFBQcwAoYjaHR0cDovL2NlcnQuaW50LXgzLmxldHNlbmNyeXB0Lm9yZy8w IwYDVR0RBBwwGoIMKi5ub3d0aW1lLmNjggpub3d0aW1lLmNjMEwGA1UdIARFMEMw CAYGZ4EMAQIBMDcGCysGAQQBgt8TAQEBMCgwJgYIKwYBBQUHAgEWGmh0dHA6Ly9j cHMubGV0c2VuY3J5cHQub3JnMIIBBQYKKwYBBAHWeQIEAgSB9gSB8wDxAHcA8JWk WfIA0YJAEC0vk4iOrUv+HUfjmeHQNKawqKqOsnMAAAFy9G9x2QAABAMASDBGAiEA 8n8ykwTPO0QKEFt6jJeJtfBn2cBMH2iPCHERy1CrR3ACIQDwPZs3YoWk1BlqIeC7 LugFyfjwCwmSKdXY+Ns/s9cdqgB2ALIeBcyLos2KIE6HZvkruYolIGdr2vpw57JJ Uy3vi5BeAAABcvRvcc4AAAQDAEcwRQIgYW1/ISr9EJY7banQGDSs95RDQcNpE2uh 5pQi2jzRPTMCIQDpzJxIk9YmETGfrqkBnhYHszrtnlZ5P2ThSRs3lpOJTjANBgkq hkiG9w0BAQsFAAOCAQEAMLVoRspbIOTy72LPBshrWGF3P3o5Z85mhRwKeCHd4w6/ XH3gopnKlQ6epNK/DkviXm+S71q3CgJloLze0PKULG9SkuRBA4LJKrP+QU6xMUgh W9HqjOU6/+CqOtEMsQqVda7jCwUygLLhpcZJVGx3AiEGnivcUYZnlFraJyFXVe5Z TDZSUAvcqxduWspfec3jKxdEt+CfLf1+Um1+n1Wid1PWHQzw0ycBYCm3DGKFrtDI LRsaSaUGH7BdbjHJ/A0380xv6Nb86NdAqT273Wpo97IHA/6H4LNV94pe5hawpht8 Qw2m6DohubBYXBf+4AlgJKZFSPxWdHOd66kD0rBOAg== -----END CERTIFICATE----- 1 s:C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3 i:O = Digital Signature Trust Co., CN = DST Root CA X3 -----BEGIN CERTIFICATE----- MIIEkjCCA3qgAwIBAgIQCgFBQgAAAVOFc2oLheynCDANBgkqhkiG9w0BAQsFADA/ MSQwIgYDVQQKExtEaWdpdGFsIFNpZ25hdHVyZSBUcnVzdCBDby4xFzAVBgNVBAMT DkRTVCBSb290IENBIFgzMB4XDTE2MDMxNzE2NDA0NloXDTIxMDMxNzE2NDA0Nlow SjELMAkGA1UEBhMCVVMxFjAUBgNVBAoTDUxldCdzIEVuY3J5cHQxIzAhBgNVBAMT GkxldCdzIEVuY3J5cHQgQXV0aG9yaXR5IFgzMIIBIjANBgkqhkiG9w0BAQEFAAOC AQ8AMIIBCgKCAQEAnNMM8FrlLke3cl03g7NoYzDq1zUmGSXhvb418XCSL7e4S0EF q6meNQhY7LEqxGiHC6PjdeTm86dicbp5gWAf15Gan/PQeGdxyGkOlZHP/uaZ6WA8 SMx+yk13EiSdRxta67nsHjcAHJyse6cF6s5K671B5TaYucv9bTyWaN8jKkKQDIZ0 Z8h/pZq4UmEUEz9l6YKHy9v6Dlb2honzhT+Xhq+w3Brvaw2VFn3EK6BlspkENnWA a6xK8xuQSXgvopZPKiAlKQTGdMDQMc2PMTiVFrqoM7hD8bEfwzB/onkxEz0tNvjj /PIzark5McWvxI0NHWQWM6r6hCm21AvA2H3DkwIDAQABo4IBfTCCAXkwEgYDVR0T AQH/BAgwBgEB/wIBADAOBgNVHQ8BAf8EBAMCAYYwfwYIKwYBBQUHAQEEczBxMDIG CCsGAQUFBzABhiZodHRwOi8vaXNyZy50cnVzdGlkLm9jc3AuaWRlbnRydXN0LmNv bTA7BggrBgEFBQcwAoYvaHR0cDovL2FwcHMuaWRlbnRydXN0LmNvbS9yb290cy9k c3Ryb290Y2F4My5wN2MwHwYDVR0jBBgwFoAUxKexpHsscfrb4UuQdf/EFWCFiRAw VAYDVR0gBE0wSzAIBgZngQwBAgEwPwYLKwYBBAGC3xMBAQEwMDAuBggrBgEFBQcC ARYiaHR0cDovL2Nwcy5yb290LXgxLmxldHNlbmNyeXB0Lm9yZzA8BgNVHR8ENTAz MDGgL6AthitodHRwOi8vY3JsLmlkZW50cnVzdC5jb20vRFNUUk9PVENBWDNDUkwu Y3JsMB0GA1UdDgQWBBSoSmpjBH3duubRObemRWXv86jsoTANBgkqhkiG9w0BAQsF AAOCAQEA3TPXEfNjWDjdGBX7CVW+dla5cEilaUcne8IkCJLxWh9KEik3JHRRHGJo uM2VcGfl96S8TihRzZvoroed6ti6WqEBmtzw3Wodatg+VyOeph4EYpr/1wXKtx8/ wApIvJSwtmVi4MFU5aMqrSDE6ea73Mj2tcMyo5jMd6jmeWUHK8so/joWUoHOUgwu X4Po1QYz+3dszkDqMp4fklxBwXRsW10KXzPMTZ+sOPAveyxindmjkW8lGy+QsRlG PfZ+G6Z6h7mjem0Y+iWlkYcV4PIWL1iwBi8saCbGS5jN2p8M+X+Q7UNKEkROb3N6 KOqkqm57TH2H3eDJAkSnh6/DNFu0Qg== -----END CERTIFICATE----- --- Server certificate subject=CN = nowtime.cc issuer=C = US, O = Let's Encrypt, CN = Let's Encrypt Authority X3 --- No client certificate CA names sent Peer signing digest: SHA256 Peer signature type: RSA-PSS Server Temp Key: X25519, 253 bits --- SSL handshake has read 3114 bytes and written 392 bytes Verification error: unable to get local issuer certificate --- New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384 Server public key is 2048 bit Secure Renegotiation IS NOT supported Compression: NONE Expansion: NONE No ALPN negotiated Early data was not sent Verify return code: 20 (unable to get local issuer certificate) --- --- Post-Handshake New Session Ticket arrived: SSL-Session: Protocol : TLSv1.3 Cipher : TLS_AES_256_GCM_SHA384 Session-ID: 4AA5922EF7050399E3A09DCE51155BB98B51EE253019EFB444C62DA6023B3C2F Session-ID-ctx: Resumption PSK: B9B0D50AEFB17628674208CEB490771BBF8130E89DBA67F9BA9B902BEFA2F45658C35A21589F43239DC2672149F8F300 PSK identity: None PSK identity hint: None SRP username: None TLS session ticket lifetime hint: 600 (seconds) TLS session ticket: 0000 - e0 1c ce db 80 2b cd b1-11 af 49 73 0b 96 ab cc .....+....Is.... 0010 - 4e 25 40 e0 ea 0f 87 25-03 e8 80 6c 92 62 c6 6a N%@....%...l.b.j 0020 - 1e 56 56 2c 10 e4 ad c8-90 4b 68 4c 4d e0 ac 69 .VV,.....KhLM..i 0030 - 13 d1 fa aa 8a b4 29 05-50 12 cf d4 3f e6 1e 08 ......).P...?... 0040 - 69 a3 0c a7 12 47 af 21-a6 e0 85 83 45 d3 c6 c3 i....G.!....E... 0050 - be 72 19 aa db ec 04 ab-d3 33 0c 1b 92 db 3a 5b .r.......3....:[ 0060 - 1a 5e c6 ff 61 68 87 fa-e0 00 ce 43 94 b4 5c 64 .^..ah.....C..\d 0070 - 86 7f 56 88 ee 71 91 0b-b3 41 12 0d ae 77 b4 df ..V..q...A...w.. 0080 - 61 84 0c 76 bf 12 70 f2-3d b8 b1 48 cd ff e2 7b a..v..p.=..H...{ 0090 - ac d8 65 f8 61 c7 e7 8e-d3 06 98 35 fd d5 11 95 ..e.a......5.... 00a0 - 91 a2 d8 95 fc b9 5d ed-c2 4b 5d 45 d0 6e 02 99 ......]..K]E.n.. 00b0 - b1 2d a5 86 31 54 06 e1-7c 60 dc 81 01 49 9a 0b .-..1T..|`...I.. 00c0 - 50 56 87 8d 3b 55 4d 8e-53 db c6 46 59 70 bf d1 PV..;UM.S..FYp.. 00d0 - b6 22 d5 36 71 66 d9 69-5d 91 3d 82 78 f7 3a d1 .".6qf.i].=.x.:. Start Time: 1594276699 Timeout : 7200 (sec) Verify return code: 20 (unable to get local issuer certificate) Extended master secret: no Max Early Data: 0 --- read R BLOCK --- Post-Handshake New Session Ticket arrived: SSL-Session: Protocol : TLSv1.3 Cipher : TLS_AES_256_GCM_SHA384 Session-ID: C937B1E7244B66542A204A57B63B6EECBEA34922740ACF0E95F8CEE676DAFE80 Session-ID-ctx: Resumption PSK: 44BC6A3EB2CF2FEC82C1C08C58F25601921C3E8558AFA17ECF37B802B9A02E22B3537B267545803903764156A16FABB6 PSK identity: None PSK identity hint: None SRP username: None TLS session ticket lifetime hint: 600 (seconds) TLS session ticket: 0000 - e0 1c ce db 80 2b cd b1-11 af 49 73 0b 96 ab cc .....+....Is.... 0010 - 24 07 ff 06 ff 62 e9 3c-fd 31 a1 93 c9 6b 5e 32 $....b.<.1...k^2 0020 - 9f 77 1f 67 1a 95 44 e6-00 73 8f ac 0f 90 37 6f .w.g..D..s....7o 0030 - 6f a1 16 62 50 64 d7 0e-20 1f 5f 75 9f 47 85 98 o..bPd.. ._u.G.. 0040 - 84 d9 7b 7f e3 43 a9 d1-4e 58 4d 58 5f 19 8f fb ..{..C..NXMX_... 0050 - 4b d1 41 6b 93 45 27 8b-e0 7d a1 64 9b 2a f4 10 K.Ak.E'..}.d.*.. 0060 - b3 28 96 49 40 6f 88 27-4f b3 21 5a 38 3e c6 3c .(.I@o.'O.!Z8>.< 0070 - e8 43 f3 eb 69 e7 da be-c4 9a 64 b4 75 ad 79 69 .C..i.....d.u.yi 0080 - 14 4e f8 1f cb 38 5f 33-80 18 ea b4 61 a9 ce ae .N...8_3....a... 0090 - 2d 43 66 83 dc 81 4c 15-7e d7 d3 8e 43 25 b2 16 -Cf...L.~...C%.. 00a0 - b0 a5 3d a4 1a f6 2b 5c-79 4b 83 46 77 ec 55 d3 ..=...+\yK.Fw.U. 00b0 - 6b c5 ee 0f 17 46 3a c9-be 90 1f 07 f2 fc e9 2f k....F:......../ 00c0 - 67 a5 de d8 ba 1f 6e 75-bb 74 42 b9 35 48 49 98 g.....nu.tB.5HI. 00d0 - 85 25 b9 52 a5 05 e6 7e-e6 b2 5e 20 6e f9 38 35 .%.R...~..^ n.85 Start Time: 1594276699 Timeout : 7200 (sec) Verify return code: 20 (unable to get local issuer certificate) Extended master secret: no Max Early Data: 0 --- read R BLOCK ``` --- # 假设我们要查看 `authme.wechall.net` 的证书,其 https 端口为 443 执行命令如下: ``` openssl s_client -showcerts -connect authme.wechall.net:443 ``` # 运行结果: ``` C:\Users\chuwen>openssl s_client -showcerts -connect authme.wechall.net:443 CONNECTED(00000180) depth=1 C = DE, ST = LowerSaxony, L = Peine, O = WeChall, OU = development, CN = gizmore, emailAddress = gizmore@wechall.net verify error:num=19:self signed certificate in certificate chain verify return:1 depth=1 C = DE, ST = LowerSaxony, L = Peine, O = WeChall, OU = development, CN = gizmore, emailAddress = gizmore@wechall.net verify return:1 depth=0 C = DE, ST = LowerSaxony, L = Frankfurt, O = WeChall, OU = development, CN = authme.wechall.net, emailAddress = gizmore@wechall.net verify return:1 13132:error:14094410:SSL routines:ssl3_read_bytes:sslv3 alert handshake failure:ssl\record\rec_layer_s3.c:1536:SSL alert number 40 --- Certificate chain 0 s:C = DE, ST = LowerSaxony, L = Frankfurt, O = WeChall, OU = development, CN = authme.wechall.net, emailAddress = gizmore@wechall.net i:C = DE, ST = LowerSaxony, L = Peine, O = WeChall, OU = development, CN = gizmore, emailAddress = gizmore@wechall.net -----BEGIN CERTIFICATE----- MIIELjCCA5cCCQDHMTcVkx1X2jANBgkqhkiG9w0BAQUFADCBkTELMAkGA1UEBhMC REUxFDASBgNVBAgTC0xvd2VyU2F4b255MQ4wDAYDVQQHEwVQZWluZTEQMA4GA1UE ChMHV2VDaGFsbDEUMBIGA1UECxMLZGV2ZWxvcG1lbnQxEDAOBgNVBAMTB2dpem1v cmUxIjAgBgkqhkiG9w0BCQEWE2dpem1vcmVAd2VjaGFsbC5uZXQwHhcNMTQwNzI5 MDk0NjUzWhcNMjQwNzMxMDk0NjUzWjCBoDELMAkGA1UEBhMCREUxFDASBgNVBAgT C0xvd2VyU2F4b255MRIwEAYDVQQHEwlGcmFua2Z1cnQxEDAOBgNVBAoTB1dlQ2hh bGwxFDASBgNVBAsTC2RldmVsb3BtZW50MRswGQYDVQQDExJhdXRobWUud2VjaGFs bC5uZXQxIjAgBgkqhkiG9w0BCQEWE2dpem1vcmVAd2VjaGFsbC5uZXQwggIiMA0G CSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQDfO6q9GnmHp3zsG+s2HJ/TJc3d5BhL 0UV+6PzfZSY5MFEg76wHPTsrasdn8z8uWQeMWprL3h4EWOlXW3YG9UOLjdvxkxL1 5vLJrxYdCu6jQ+KvoJtRzFXUDZcKjpDfnibgrUc18HW35FF5i2FkTpRFVP0p6INu m8FsyHfN3NfytDBAZLNqBIDtNvXdZQKRDiJp/90x2Bgj0/TiiO6TzmX0f7Vt5ogb ft6OhwsQm1HRzA1st1dpi0rTHM5bYw+ulldkY7ILrpES3sSukCBe1dVYxgzXM5xo 09iyPZkXzh+4h+J9Lt4rJlWWvlZJ6qoaC/bWrQE7U0JB9B/GFykguewaIt5QUMEx njAyTEFzief4209mnCpysoq/yRyRygEMrAGW0jzhmyNWkrvvOiaygT2jICywBMbn /wn8hQgxwDj5903xUdqtlLjgItcKMQNW3FvurjvDvuS/Vo5X+cQPZFluj28azRZ8 AUKwGuDCp4OiinJRukokC+kY+qLLSbxR9NhVq0Vi6+T/xHKazOwCCZ0w9T7eCldF OV7Yd85S8FtI0CvD5egs04OfCdnAMW2DK+JGTcSLmdbPGTddk4je9Oqi6QnVi2Yv hNBaupEOAknl6Yo+bQEXaMwi1sS3uhpmrIxu5p8jdtb4qCkxRcl9dJcUSn/HWK7/ YrgbgPMYMjfA5wIDAQABMA0GCSqGSIb3DQEBBQUAA4GBAKiXqEGzNnPq0MxqQLcq TxOF7H83MIXbHCIM4tJliYRm5wIs/Xg9koBT0Oi2PVXud3a/oOH0NBJTYF8bD0v0 s90fY8496QJs9BSVbTu4QWNZyvFpefBaO1fb0xeGlXFR8GHbUZ73rGLHE9qbZGrX N7OyHBB6X0gXZ8lZ8nS49k3o -----END CERTIFICATE----- 1 s:C = DE, ST = LowerSaxony, L = Peine, O = WeChall, OU = development, CN = gizmore, emailAddress = gizmore@wechall.net i:C = DE, ST = LowerSaxony, L = Peine, O = WeChall, OU = development, CN = gizmore, emailAddress = gizmore@wechall.net -----BEGIN CERTIFICATE----- MIIDnDCCAwWgAwIBAgIJAMQYS3CTzcElMA0GCSqGSIb3DQEBBQUAMIGRMQswCQYD VQQGEwJERTEUMBIGA1UECBMLTG93ZXJTYXhvbnkxDjAMBgNVBAcTBVBlaW5lMRAw DgYDVQQKEwdXZUNoYWxsMRQwEgYDVQQLEwtkZXZlbG9wbWVudDEQMA4GA1UEAxMH Z2l6bW9yZTEiMCAGCSqGSIb3DQEJARYTZ2l6bW9yZUB3ZWNoYWxsLm5ldDAeFw0x NDA3MjkwOTA3MTRaFw0yNDA3MzEwOTA3MTRaMIGRMQswCQYDVQQGEwJERTEUMBIG A1UECBMLTG93ZXJTYXhvbnkxDjAMBgNVBAcTBVBlaW5lMRAwDgYDVQQKEwdXZUNo YWxsMRQwEgYDVQQLEwtkZXZlbG9wbWVudDEQMA4GA1UEAxMHZ2l6bW9yZTEiMCAG CSqGSIb3DQEJARYTZ2l6bW9yZUB3ZWNoYWxsLm5ldDCBnzANBgkqhkiG9w0BAQEF AAOBjQAwgYkCgYEAvdoWtpmxsCyhl8BFeZVqVk0JmVrkfls/uQVjzGiZ/9gV8G9A REhNpQSWIBNdC52qv9xDVJmgGLAJhDL0Qhh7ia4F9W3Gt9ZOjGs4zT7ZkJwdr9r/ 1N+7kwt1bd5pUEEiNHrqWppK9nh4DWueoOl/kGpOXRODkrR9lAdWnD+y4Z0CAwEA AaOB+TCB9jAdBgNVHQ4EFgQUNGqLUeVuzA8iVTd94saA6ALAWMIwgcYGA1UdIwSB vjCBu4AUNGqLUeVuzA8iVTd94saA6ALAWMKhgZekgZQwgZExCzAJBgNVBAYTAkRF MRQwEgYDVQQIEwtMb3dlclNheG9ueTEOMAwGA1UEBxMFUGVpbmUxEDAOBgNVBAoT B1dlQ2hhbGwxFDASBgNVBAsTC2RldmVsb3BtZW50MRAwDgYDVQQDEwdnaXptb3Jl MSIwIAYJKoZIhvcNAQkBFhNnaXptb3JlQHdlY2hhbGwubmV0ggkAxBhLcJPNwSUw DAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQUFAAOBgQCLt0cRKdertOduwl/jfwlT 2eadw5dBtCryDO9d5PTWTkJl89MyYmQszj4Kx7NC2Yc3JklLI2q+XSgTdzn7VJ1W HM4sC8XboLQttzBkI160Jgl/dYNcjX22vH2h4W8bGlAnq3MCMrjZnFhgWQTosJWh qovBkUnH+FVo7S9eW+60hg== -----END CERTIFICATE----- --- Server certificate subject=C = DE, ST = LowerSaxony, L = Frankfurt, O = WeChall, OU = development, CN = authme.wechall.net, emailAddress = gizmore@wechall.net issuer=C = DE, ST = LowerSaxony, L = Peine, O = WeChall, OU = development, CN = gizmore, emailAddress = gizmore@wechall.net --- Acceptable client certificate CA names C = DE, ST = LowerSaxony, L = Brunswick, O = CSTx, OU = development, CN = authme.wechall.net, emailAddress = christian@wechall.net C = DE, ST = LowerSaxony, L = Peine, O = WeChall, OU = development, CN = gizmore, emailAddress = gizmore@wechall.net Client Certificate Types: RSA sign, DSA sign, ECDSA sign Requested Signature Algorithms: RSA+SHA512:DSA+SHA512:ECDSA+SHA512:RSA+SHA384:DSA+SHA384:ECDSA+SHA384:RSA+SHA256:DSA+SHA256:ECDSA+SHA256:RSA+SHA224:DSA+SHA224:ECDSA+SHA224:RSA+SHA1:DSA+SHA1:ECDSA+SHA1 Shared Requested Signature Algorithms: RSA+SHA512:DSA+SHA512:ECDSA+SHA512:RSA+SHA384:DSA+SHA384:ECDSA+SHA384:RSA+SHA256:DSA+SHA256:ECDSA+SHA256:RSA+SHA224:DSA+SHA224:ECDSA+SHA224:RSA+SHA1:DSA+SHA1:ECDSA+SHA1 Peer signing digest: SHA256 Peer signature type: RSA Server Temp Key: ECDH, P-256, 256 bits --- SSL handshake has read 3056 bytes and written 458 bytes Verification error: self signed certificate in certificate chain --- New, TLSv1.2, Cipher is ECDHE-RSA-AES256-GCM-SHA384 Server public key is 4096 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE No ALPN negotiated SSL-Session: Protocol : TLSv1.2 Cipher : ECDHE-RSA-AES256-GCM-SHA384 Session-ID: Session-ID-ctx: Master-Key: 1633D25BB4F817A340857CAF0C283284468941EF791EFDAF62E7F79FFE9C49C1727C5B78DF0DAC36A5C4BAD62CC6FDBB PSK identity: None PSK identity hint: None SRP username: None Start Time: 1594276479 Timeout : 7200 (sec) Verify return code: 19 (self signed certificate in certificate chain) Extended master secret: no --- ```